Authentications overview
Authentication is the process of verifying the identity of users who request access to a device, system, or network. Vymo employs various authentication methods to ensure secure access:
-
Password-based Authentication: This method involves user names and passwords set up directly in Vymo. If the credentials match with the Vymo database, access is granted. This protocol operates independently without needing any third-party integration, referred to as Vymo authentication.
-
REST API Authentication with LDAP: In this method, the customer sets up its LDAP service, and Vymo connects to this service through REST API to validate the user credentials stored on the customer's LDAP server. This integrates with the directory services of customers.
-
User Authentication with OAuth 2.0: Vymo connects with third-party applications like Office365, Google Workspace, Salesforce, and Azure Active Directory using OAuth 2.0, an authorization protocol that requires explicit user permission.
-
User Authentication with SAML: Similar to OAuth 2.0, this method uses SAML (Security Assertion Markup Language) for connecting with third-party applications like Azure Active Directory. It is an XML-based open-standard for transferring identity data between an identity provider (IdP) and a service provider (SP).
Multiple Authentication Types
These authentication protocols operate at the user level, not at the customer level. This means, within the same customer, some users can use Vymo authentication while others might use REST API authentication.
2FA Supported
Vymo supports two-factor authentication, adding an extra layer of security by using two methods consecutively to verify a user's identity. Learn more about this in two-factor authentication.
Vymo Authentication Process
Vymo authentication is a two-step process:
This step is initiated when a Vymo user enters their login ID. The information is sent in an encrypted format to Vymo servers for validation.
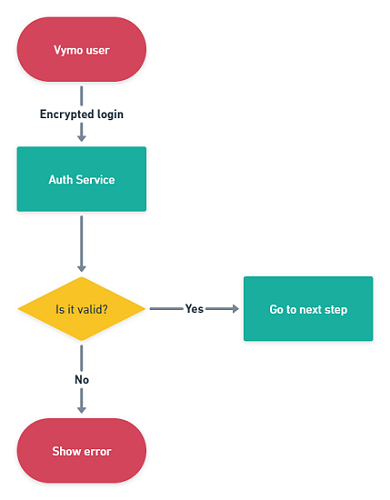
This step occurs when a Vymo user enters their password. The information is encrypted and sent to Vymo servers. If a match is found, a user session is created.

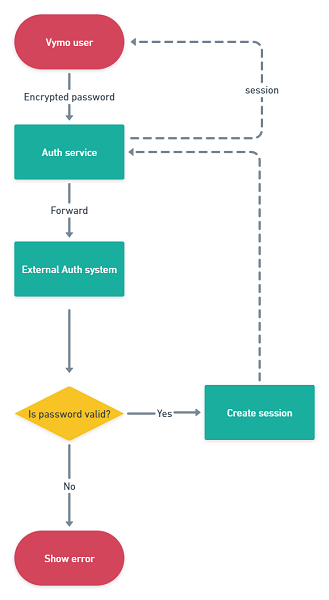
LDAP authentication
This guide outlines the two-step LDAP authentication process for Vymo users and provides instructions for setting up the password reset feature via an external deep link, tailored specifically for LDAP authenticated users.
The process begins when a user inputs their login ID in the Vymo app, initiating the user validation process. This step adheres to the standard Vymo authentication procedure to confirm the user's identity, ensuring they are registered within the Vymo system.

- Password Entry: After user validation, the user enters their password. This password is encrypted for security before transmission.
- Transmission Method: The encrypted data is sent securely to the customer's LDAP server using a REST call. This ensures data remains confidential during transmission.
-
Customization: The format of the REST call, both request and response, is customized to fit each customer's specific LDAP configuration. This enhances compatibility and strengthens overall security.
Setting Up Password Reset via External Deep Link
To accommodate users authenticated through LDAP, integrating a password reset feature via an external deep link is essential. This setup involves the following steps:
- Configure the Deep Link: Set up the deep link to interact properly with the LDAP server, including the correct URL, parameters, and authentication mechanisms.
- Integrate with Vymo: Embed the deep link in the Vymo app, typically within the user profile or settings area, allowing easy access for users to reset their passwords.
- Test the Feature: Conduct thorough testing of the deep link to ensure it communicates effectively with the LDAP server and that password resets are conducted securely and successfully.
This method ensures a secure, reliable process for users to manage their authentication credentials within the Vymo app, enhancing both security and user experience.
OAuth 2.0 authentication
This guide outlines the OAuth 2.0 authentication process for Vymo users, covering the two-step authentication process and implementation considerations. Additionally, example codes for various scenarios are provided to assist in the integration and usage of OAuth 2.0 with Vymo.
Trigger: The authentication process initiates when a Vymo user inputs their login ID. This action triggers a redirect to the OAuth 2.0 service provider.
Authentication and Code Retrieval: If the authentication is successful, the OAuth 2.0 service returns an authorization code to Vymo. This code is crucial as it is used in the next step to obtain an access token.

Automatic Trigger: This step follows immediately after successful user authentication. It does not require any manual input from the user as it is automatically triggered by the prior step's completion.
Token Request and Session Creation: Using the previously obtained authorization code, the Vymo server requests an access token from the OAuth 2.0 service. Once the access token is received, it is used to verify the user's identity. Upon successful verification, a session is created for the user. This session remains active until the user logs out, maintaining a secure connection throughout the user's interaction with the application.

Implementation Considerations
Implementing OAuth 2.0 authentication involves understanding the specific requirements and settings of the OAuth provider being used. Below are key considerations:
- Secure Storage of Credentials: Ensure that client secrets and other sensitive data are securely stored and not exposed within client-side code.
- Consistent Session Management: Manage user sessions efficiently to ensure that access tokens are refreshed as needed and sessions are securely closed upon user logout.
- Error Handling: Implement robust error handling to manage and respond to authentication errors, such as expired tokens or unauthorized access attempts.
The following table shows a comparison of what can be implemented in Vymo through the available authentication methods.
| OAuth 2.0 | LDAP | Vymo | |
|---|---|---|---|
| Works on the web | Yes | Yes | Yes |
| Works on a phone | Yes | Yes | Yes |
| Password entry on Vymo screen | No | Yes | Yes |
| 1-tap login | No | No | Yes |
| Pre-authenticated login | No | Yes | No |
| Lock the user account if an incorrect password is entered a specific number of times | Yes | Yes | Yes |
| Force a change in the password after a specific time interval | No | No | Yes |
| Specify a list of devices that people can log in from | Yes | Yes | Yes |
| Specify a list of IPs that people can log in from | Yes | Yes | Yes |
| Allow multiple session login at a time | Yes | No | No |
Integrations
The Vymo authentication method needs no integration with any other application. For the other two methods, the following integrations are available.
- Azure Active Directory
- Salesforce
- REST API
Setting up authentication
To set up an authentication system of your choice, contact Vymo Support.